Top 10 Mobile App Security Threats

With mobile apps expected to reach more than 183.7 billion installations globally, there has also been an increase in mobile app security threats. Today’s cyberattacks are highly sophisticated, requiring constant vigilance due to many unknown or emerging threats. These threats require a proactive approach to mobile application security.
End users can take steps to protect sensitive data on their devices, such as avoiding unprotected public Wi-Fi and setting up multi-factor authentication. However, for developers, it is a much more complicated task.
In this article, we will examine the top ten security threats to mobile applications and discuss strategies and best practices for addressing them.
Top 10 Security Threats For Mobile Apps
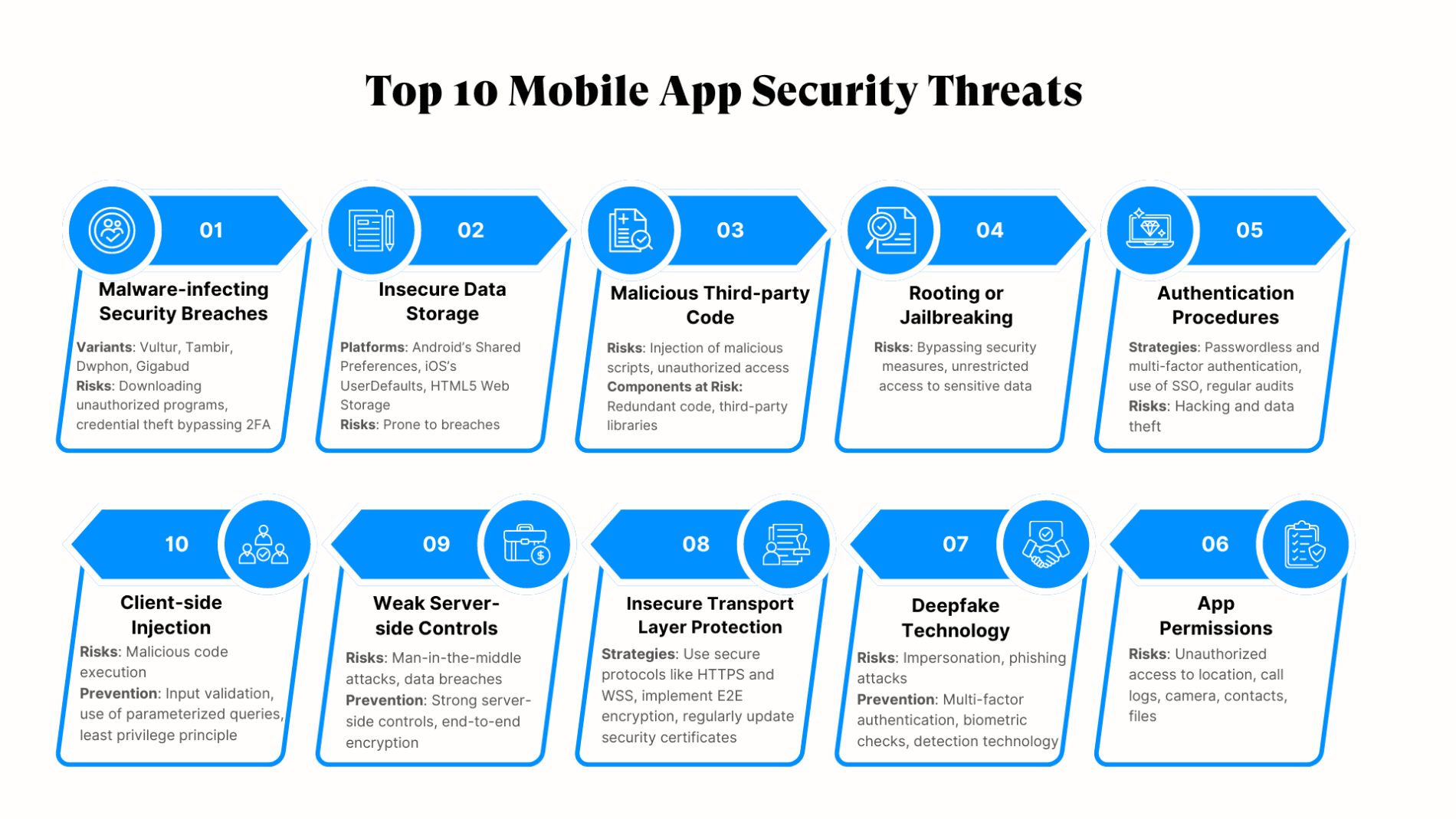
1. Malware-infecting Security Breaches
Malware has evolved significantly over the past few years. Vultur, a shape-shifting banking malware, was identified as a threat, but by 2024, it had developed new capabilities to control Android devices.
Another alarming trend is the rise of Tambir, Dwphon, and Gigabud, three new and concerning Android malware variants causing mobile app security issues. A malicious program can pose mobile application security risks to a user’s privacy and security, including downloading other programs, credential theft, and bypassing two-factor authentication (2FA).
As these malicious programs diversify, they are growing into mobile application security risks. Therefore, maintaining constant surveillance and detecting such threats is crucial to detecting and preventing these threats.
How To Prevent Malware Attacks
As malware attacks evolve, best practices must be adopted to protect against them.
- Update Software Regularly: Updates often include patches for security vulnerabilities that malware can exploit. Ensure you update your software regularly, including your operating system, apps, and security software.
- Be Cautious With Downloads: Download apps only from trusted sources, and beware of unreliable email attachments and links.
- Reputable Security Solution: A good security app can help detect and remove malware and provide real-time protection.
2. Insecure Data Storage
Developers often turn to client storage for data, including platforms like Android’s Shared Preferences, iOS’s UserDefaults, and HTML5 Web Storage for web applications. However, these storage methods are prone to security breaches.
The best strategy for securing data stored across these platforms is to add layer of encryption to the operating system’s base encryption. A further degree of security can be achieved by using specialized hardware, such as iOS’ Secure Enclave or Android’s TrustZone technology.
How to Prevent the Loss of Data
An integrated approach is required for data safety. Here is how you can prevent data loss:
- The first step is to limit the scope of data storage. Excessive data storage can lead to security vulnerabilities, so it is important to limit data storage to the minimum required.
- Secondly, use strong encryption methods. A layer of encryption can be added over the operating system’s base level, and specialized hardware features may be utilized if available.
- Thirdly, regularly update and patch your systems. Keeping your software up-to-date ensures that you have the latest security enhancements and fixes for known vulnerabilities.
- Lastly, educate your team about the importance of data security. Everyone involved in the development process should understand the potential risks and best practices for data protection.
3. Malicious third-party code
Developers often use third-party code to speed up development and incorporate advanced functionalities. However, there are risks associated with this:
- Redundant Code: During the development of complex applications, developers may leave behind code that is no longer required or relevant. Not managing and removing redundant code can create a security loophole. Attackers can inject malicious scripts or gain unauthorized access when they discover unused code.
- Third-Party Libraries: Developers frequently use third-party libraries, such as React Native for cross-platform development, Glide for image loading in Android apps, or Alamofire for networking in iOS apps. If your mobile app integrates with a third-party library, ensure that it is from a reputable source, regularly updated, and free of known security vulnerabilities.
How to Protect Against Malicious Code
Adopt a comprehensive security strategy to safeguard against malicious code. Regularly review and clean up your codebase, removing any redundant or unused code. Please exercise caution when integrating third-party libraries, ensuring they are regularly updated from trusted sources.
Utilize static and dynamic analysis tools to detect potential security issues in your code. Lastly, educate your team about secure coding practices and third-party code risks.
4. Rooting Or Jailbreaking
Rooting or jailbreaking is a process that involves gaining superuser or root access to a device’s operating system, essentially removing all restrictions imposed by the device manufacturer. Although this action has some attractive features and functionality, it carries some risks as well significant security risks that should not be overlooked.
Rooted or jailbroken devices may have their inherent security measures bypassed, potentially allowing malicious software to operate. Devices typically have built-in safeguards to defend against such threats.
However, with root access, these protective measures can be bypassed, which allows unauthorized code to operate freely.
How To Stop Users Jailbreaking
Companies can take several steps to educate and prevent users from jailbreaking their phones. Here are some strategies:
- Promote Official App Stores: Advise users to download apps only from official app stores, which have strict security protocols and app review processes in place. Highlight the dangers of downloading apps from third-party sources, which often host pirated apps that may require a jailbroken device.
- Regular Software Updates: Regularly update the operating system and apps to patch any security vulnerabilities that could be exploited for jailbreaking. Make sure users are aware of the importance of keeping their software up-to-date.
- Implement Detection Mechanisms: Use software to detect if a device has been jailbroken. If a jailbroken device is detected, the company can prevent access to certain sensitive apps or data.
5. Authentication procedures
A robust end-to-end encryption must now be used for every step of the connection, from the mobile device to the server. This involves using authentication protocols, which are sets of rules and procedures that verify the identity of a user or device accessing a mobile app.
Authentication systems are largely determined by the authentication technology deployed and the number of factors they incorporate. However, no authentication protocol is 100 percent foolproof.
Therefore, it’s important to choose the method carefully to reduce the risk of hacking and data theft. As more critical information is stored electronically and as hackers become more adept at theft, authentication becomes increasingly essential.
How To Improve Secure Authentication
To improve secure authentication measures in mobile apps, consider the following strategies:
- Implement Multi-Factor Authentication (MFA): MFA requires users to provide more than one piece of evidence to verify their identity. This could be a combination of something they know (like a password), something they have (like a security token), and something they are (like a fingerprint).
- Use Single Sign-On (SSO) Functionality: SSO allows users to log in once and gain access to multiple systems without being prompted to log in again. Combined with MFA, it can significantly reduce the risk of account compromise.
- Use Password Managers: Password managers can generate strong, unique passwords for each website and service, reducing the risk of password reuse and weak passwords.
- Regular Audits and Updates: Review and update your authentication strategies regularly to stay ahead of cybercriminals. This includes staying up-to-date with the latest authentication best practices and technologies.
6. App Permissions
Although app permissions are meant to protect your phone’s data by separating developers from specific segments, they often fail to do so. App stores encourage developers to clarify permissions, but these descriptions are often brief or intentionally unclear.
There are several instances of malicious permission violations, such as:
- Location Access: Once an app is granted access to location data, developers can extract direction and altitude information. In the hands of a malicious actor, this information could be used for stalking or other malicious activities.
- Call Logs: Apps with this permission can read and write phone call logs. Malicious apps could use this to spy on your call history or even make unauthorized calls.
- Camera: Used for taking photos, recording footage, and streaming video. Malicious apps could secretly take pictures or record videos without your knowledge.
- Contacts: Some apps may request to read, create, or edit your contact list and access the list of all accounts used on your device. Hackers could exploit this to send phishing emails or messages to your contacts.
- Files and Media: This permission grants access to your files, media, photos, and anything else stored on your phone’s memory. Malicious apps could use this permission to access and steal your personal files.
- Microphone: This permission allows apps to record audio. A malicious app could use it to eavesdrop on your conversations.
How To Protect Threats from Overprivileged Apps
To protect against the threats posed by overprivileged apps, consider the following strategies:
- Understand App Permissions: Before installing an app, understand what permissions it asks for. Consider it a red flag if it asks for more permissions than it needs to function.
- Use Privacy Settings: Use your device’s privacy settings to control which apps have access to what data. Review and update these settings regularly as needed.
- Install Apps from Trusted Sources: Only install apps from trusted sources like official app stores. These platforms have security measures in place to protect against malicious apps.
- Uninstall Unnecessary Apps: If you’re not using an app, uninstall it. This reduces the potential attack surface for hackers.
7. New Threat
Deepfake technology, which uses artificial intelligence to create hyper-realistic but fake audio and video content, has emerged as a new threat in the mobile app security landscape. This technology can be used to impersonate legitimate users, tricking authentication systems, and gaining unauthorized access to sensitive data.
Deepfakes can also be used to create convincing phishing attacks, tricking users into revealing their personal information or login credentials.
How To Prevent Against Deepfake Technology,
To protect against the threats posed by deep fake technology, consider the following strategies:
- Multi-Factor Authentication: Implement multi-factor authentication in your apps. This adds an extra layer of security, making it more difficult for attackers to gain access even if they’ve created a convincing deep fake.
- Biometric Authentication: Consider using biometric authentication methods, such as fingerprint or facial recognition. While not foolproof, these methods are currently more difficult for deepfake technology to bypass.
- Deepfake Detection Technology: Invest in deep fake detection technology. While still in its early stages, this technology uses machine learning to analyze audio and video content for signs of manipulation.
- User Education: Inform users about the existence of deepfake technology and how it can be used in phishing attacks. Encourage them to be skeptical of unexpected communications and to double-check the source before providing sensitive information.
8. Insecure Transport Layer Protection
The transport layer pertains to the pathway through which data is transmitted or received between the client and the server. Implementing end-to-end encryption is crucial to prevent unauthorized individuals from intercepting and reading the content. A prime example of this is the encryption used in WhatsApp’s messaging and communication.
Enhancing Transport Layer Security
To improve the security of the transport layer, consider the following strategies:
- Use Secure Protocols: Use secure protocols like HTTPS and WSS for data transmission. These protocols encrypt the data during transmission, protecting it from interception.
- Implement End-to-End Encryption: End-to-end encryption ensures that the data is encrypted on the sender’s device and only decrypted on the receiver’s device. This means that it cannot be read even if the data is intercepted during transmission.
- Regularly Update Security Certificates: Security certificates used in encryption should be regularly updated and managed to prevent them from being exploited.
- Educate Users: Inform users about the importance of using secure networks, especially when transmitting sensitive data.
9. Weak or Removed Server-Side Controls
Servers often act as the conduit for data transfer, making them prime targets for cybercriminals. These “man-in-the-middle” attacks occur when security certificate controls are bypassed, which can arise if mobile application developers deactivate security certificate verification during mobile app feature testing and neglect to reactivate it. It’s crucial to conduct controlled man-in-the-middle scenarios to identify potential vulnerabilities.
End-To-End Encryption
End-to-end encryption (E2EE) is a fundamental component of secure communication. It ensures that the information exchanged between parties remains confidential and inaccessible to potential eavesdroppers.
E2EE encodes data accessible only by the sender and recipient, safeguarding personal and business communications from unauthorized access, theft, surveillance, and tampering. The increase in sophisticated and frequent cyber attacks makes end-to-end encryption more necessary than ever.
For businesses, end-to-end encryption is imperative for compliance with regulations such as GDPR and HIPAA and is a critical component of a comprehensive cybersecurity strategy to prevent data breaches and mitigate the consequences of financial losses, legal penalties, and damage to reputation
10. Client-side Injection
Client-side injection occurs when software incorrectly processes input data as code, similar to some server-side security threats. The primary difference is that the code is dispatched to the client instead of the server. An effective approach to avoiding application injection vulnerabilities is to identify input sources and ensure that user and application-provided data are validated.
How to Prevent Application Injection Vulnerabilities
In order to prevent application injection vulnerabilities, it’s crucial to implement a few key strategies:
- Input Validation: Ensure all user and application-provided data is validated before processing. This can help prevent malicious code from being executed.
- Use of Parameterized Queries: This can help prevent SQL injection attacks by ensuring that the parameters are treated as literal values and not executable code.
- Least Privilege Principle: Limit the permissions of your applications to only what they need to function. This can help reduce the potential damage of an injection attack.
- Security Testing: Regularly test your applications for security vulnerabilities. This can help you identify and fix potential injection vulnerabilities before they can be exploited.
Best Practices For Mobile App Security Testing
Understand the Types of Penetration Tests
Penetration tests are a critical part of security testing where the tester tries to breach the system. Two main types are:
- White Box Testing: In this method, the tester has full visibility of the software’s internal structure, design, and coding. It can help identify issues like code vulnerabilities, broken paths, or security loopholes.
- Black Box Testing: In this method, the tester verifies the functionality without knowing internal workings. This method is effective in identifying security issues like data leaks, functionality errors, or server errors.
Know Your App’s Nature
The nature of your app determines the extent of security testing required. Apps dealing with sensitive data like financial transactions may require additional security measures. For instance, an e-commerce app would require strong encryption for payment processing, while a note-taking app might not need such stringent measures.
App Code and Hidden Functions
Hidden parameter codes can become vulnerabilities if left unprotected. For instance, SQL shortcuts for UI elements like text boxes and drop-down menus are often prone to SQL injection attacks. Regular code reviews and using parameterized queries can help mitigate such risks.
Use Automated Tools
Automated security testing tools can help identify common vulnerabilities quickly and efficiently. Tools like OWASP ZAP, Nessus, Wireshark can automate the process of finding common vulnerabilities like XSS, CSRF, SQL injection etc.
Perform Regular Audits
Regular security audits can help identify new vulnerabilities and ensure that the existing security measures are still effective. These audits should include a thorough review of the codebase, infrastructure, and data handling practices.
Final Thoughts
A multi-layered security approach is essential for managing malware risks, improving data security, and handling permissions effectively. In addition, server-side controls and combating deep fake technology are crucial for comprehensive security.
For developers and organizations, ongoing vigilance and proactive security measures are vital. Implementing end-to-end encryption and secure authentication methods are fundamental in mitigating risks.
Furthermore, partnering with an experienced mobile app testing company like Testlio can further enhance your security efforts. Testlio specializes in mobile app testing services that ensure your applications are functional and secure. For expert support in mobile app security, visit Testlio.com.

With thousands of validated testers in nearly 100 countries, Testlio offers a massive pool of the best QA testers in the business. Get in touch to learn more.

